How to Change Password Encryption
To change encodings, the System Administrator does the following:
Step 1: Migrate system accounts to the new password encoding.
-
Specify the new password encoder as
passwordEncoderMigrateTobean with properties:WEB-INF/config/context/security/afm_users/password-manager.xmlFor example, if you are migrating to bcrypt encryption,
passwordEncoderMigrateTobean definition will look like:<bean id="passwordEncoderMigrateTo" class="com.archibus.app.common.security.providers.dao.PasswordEncoderAdapter"> <property name="passwordEncoder"> <bean class="org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder"/> </property> </bean>
- Start Web Central with the default password encoder.
-
Load the Change Password Encoding wizard in Web Central.
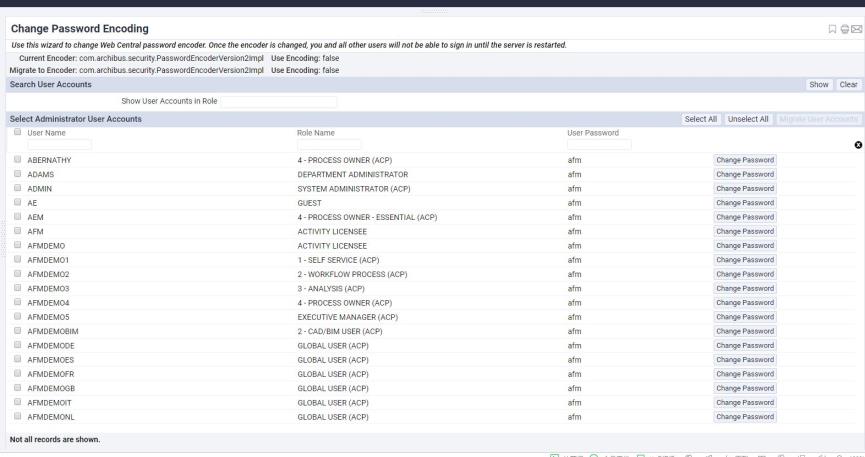
- This form has a grid with arestriction console. The default restriction is for user accounts with Archibus SYSTEM ADMINISTRATOR role. The form allows editing of the clear-text passwords. The form does not allow editing of the GUEST password.
- Edit the passwords for one or more system accounts by using the Change Password button. This action will show a pop-up dialog to get your entry and save it in the form. Regardless of your current encryption method, this dialog will save the new password in plain text.
- The Migrate User Accounts action uses a plain text password as its starting point to encrypt it. The action cannot migrate an already encrypted value (as depending on your encryption, there may not be any method of reverse-engineering such an encrypted value).
- The Migrate User Accounts action will not be active until you have changed the encryption (as until then, there is no encrypted form for the program to migrate the passwords to).
- It is essential to know the passwords to one or more system accounts, as otherwise, once you change the default encoding on startup as per step 5, you will not be able to log in again.
- Select some of the system accounts, and click the Migrate User Accounts button to migrate the encryption for these system accounts.
-
Specify the new default password encoder in WEB-INF/config/context/security/afm_users/password-encoder/archibus/password-encoder.xml.
For example, if you are migrating to bcrypt encryption,
passwordEncoderbean definition will look like:<bean id="passwordEncoder" class="com.archibus.app.common.security.providers.dao.PasswordEncoderAdapter"> <property name="passwordEncoder"> <bean class="org.springframework.security.crypto.bcrypt.BCryptPasswordEncoder"/> </property> </bean>
-
Configure WEB-INF/config/context/security/security-afm-users.xml, modified to specify desired encoding. Below is an example for SHA:
<import resource="afm_users\password-encoder\sha\password-encoder.xml" />
- Restart Web Central to have this default encoder take effect.
- If you used plain text passwords, you can use the Change Password Encoding form to encode all of your non-system user passwords.
- If you used passwords encrypted with a previous encryption method, you must reissue passwords to all users.
Step 2: Reissue passwords.
Now that you have changed the default encoding, you need to reissue passwords to users to get each user a password encrypted using new encryption settings.
-
To do so, load the Reissue Passwords Wizard in Web Central.
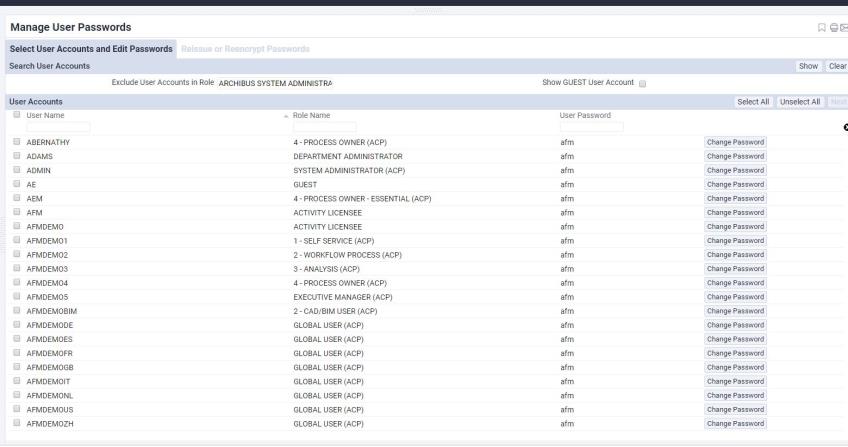
You might want to use the console to filter for all users of a particular role to reissue their passwords at one time. By default, the console filters out all ARCHIBUS SYSTEM ADMINISTRATOR accounts – as you migrated these passwords previously – and the GUEST account, which should not have its password set.
-
Select the desired users, then click Next.
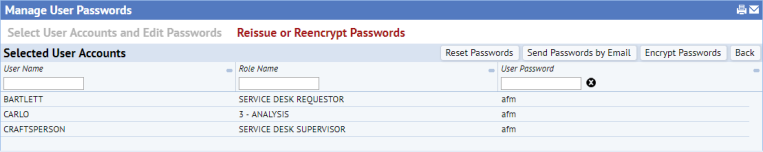
- Now you can run the following actions on all selected user accounts:
-
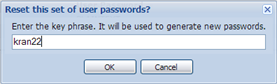
Reset Passwords. Generate new plain text passwords for these accounts. This action shows a popup that prompts you for the key phrase to use as a seed value to hash with the user name, making the resulting password difficult to reverse engineer.
- Send Passwords by Email. Send these plain text passwords to users by email. The email urges the user to log in and change the password as soon as possible.
- Encrypt Passwords. Encrypt the plain text passwords in the database – after you have sent the email to the user.
Considerations
Guest Account
If you use the GUEST account, you should:
- Enter a value for password for the GUEST account before the encryption.
- Modify the schema/ab-core/views/sign-in/ab-sign-in.js file: enter the clear password value as a string value for GUEST_PASSWORD variable.
Sample Headquarters Database
If you are working with sample HQ.DB, exclude from the password reset and re-encryption account AFM (so that the system administrator can always sign in and see important processes assigned). You can re-encrypt this value, but you should not reset it.