Authentication Use Case: LDAP
The Essential LDAP Scenario
In this scenario, user credentials are kept in an LDAP server external to Web Central.
The security service:
- Presents the login dialog.
- Receives the request with the login credentials (Username and password).
- Calls the LDAP server with the Username and password, LDAP server authenticates the user credentials.
- Loads the UserAccount object from a record in afm_users table for a given Username.
- Uses the UserAccount properties (security groups, VPAs) for the authorization.
For information on configuring this scenario, see Configuring the LDAP Authentication Use Case.
The following diagram illustrates LDAP authentication dependencies:
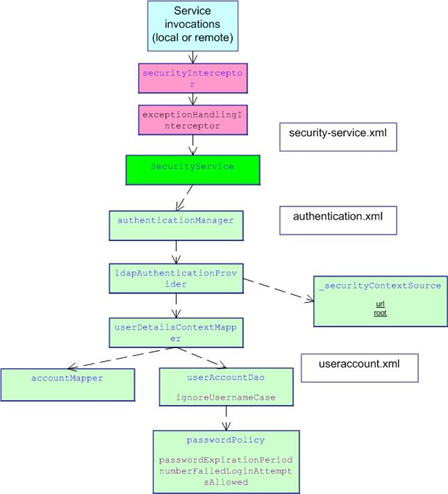
Mapping LDAP Users to Archibus Users
When you use an LDAP server for authentication, you need to map the user’s LDAP account to an Archibus account in the afm_users table.
There are three methods.
One-to-One
Active Directory (AD) users are mapped to their own unique Archibus identity. For instance, BIGUNIV\smith is mapped to the smith Archibus user, and BIGUNIV\davies is mapped to the davies Archibus user.
Many-to-One
All LDAP accounts are mapped to a single Archibus account (by default, user AFM).
Authority-by-Prefix
Each LDAP account has an authority (LDAP Group) with the specified prefix (by default, "Afm"). The LDAP Group with the specified prefix (Afm) will be used as the Archibus account name. For example:
For example:
- The BIGUNIV\smith LDAP account will be a member of the LDAP Group "Afm_Move_Mgr".
- The Archibus Security Users table (afm_users) will have a record with user_name "AFM_MOVE_MGR".
- The "AFM_MOVE_MGR" record will have a Role Name of “AFM MOVE MANAGER”.
- The "AFM MOVE MANAGER" Role will have an assigned process such as, "Assign Work".
- When BIGUNIV\smith logs in to Web Central, the security service will determine that they are a member of the "Afm_Move_Mgr" LDAP group, and log the user into Web Central as the "AFM_MOVE_MGR" user in Archibus Security Users table.