Set Up OAuth2 for Reservations and Maintenance
This step-by-step guide shows how to obtain a certificate and configure an Office 365 tenant for allowing the connection from Archibus Web Central to Exchange.
Follow these procedures in order to use Exchange integration with the Archibus Reservations and Archibus Maintenance applications.
For SMTP instructions, see Set Up OAuth2 Authentication for Archibus Extension for Microsoft Exchange.
Step 1: Register Web Central as an Application in the Office 365 Tenant
-
Sign in to the Microsoft Azure Portal at https://aad.portal.azure.com/ using an Office 365 admin account on the home tenant.
-
Navigate to Azure Active Directory > App Registrations > New registration.
-
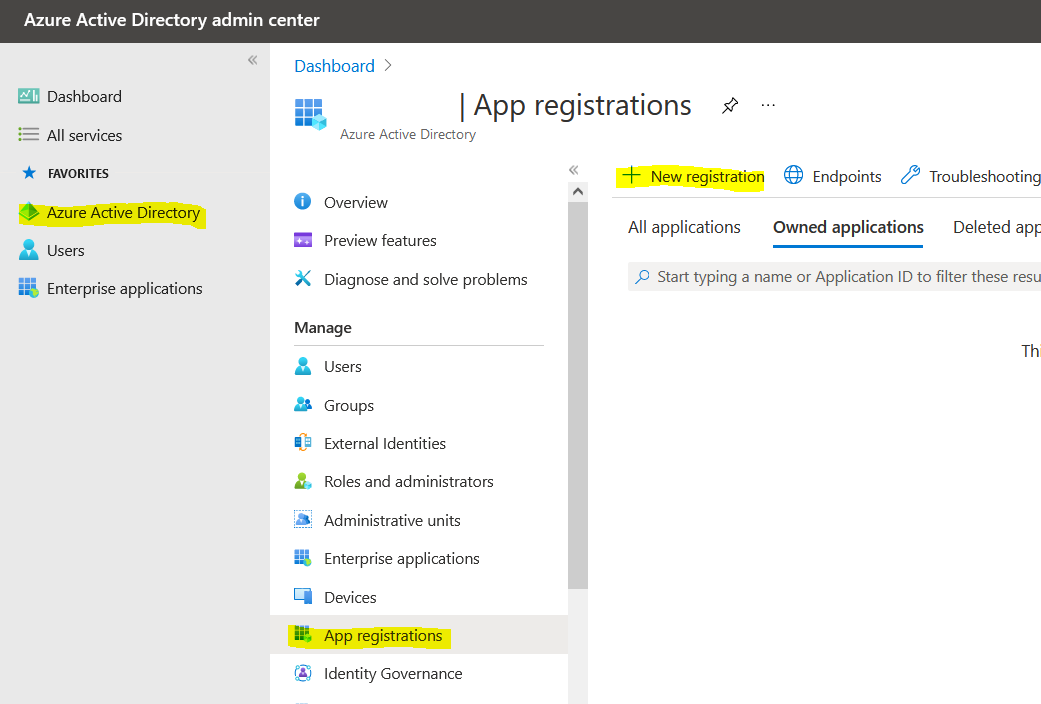
On the registration screen:
-
Enter an application name.
-
If the application will only be used for this single tenant, select "Accounts in this organizational directory."
-
If the application needs access to multiple tenants, select "Accounts in any organizational directory."
(This is selected in red in the iimage below). -
Enter
https://aad.portal.azure.comas the redirect URL. -
Click Register.
-
-
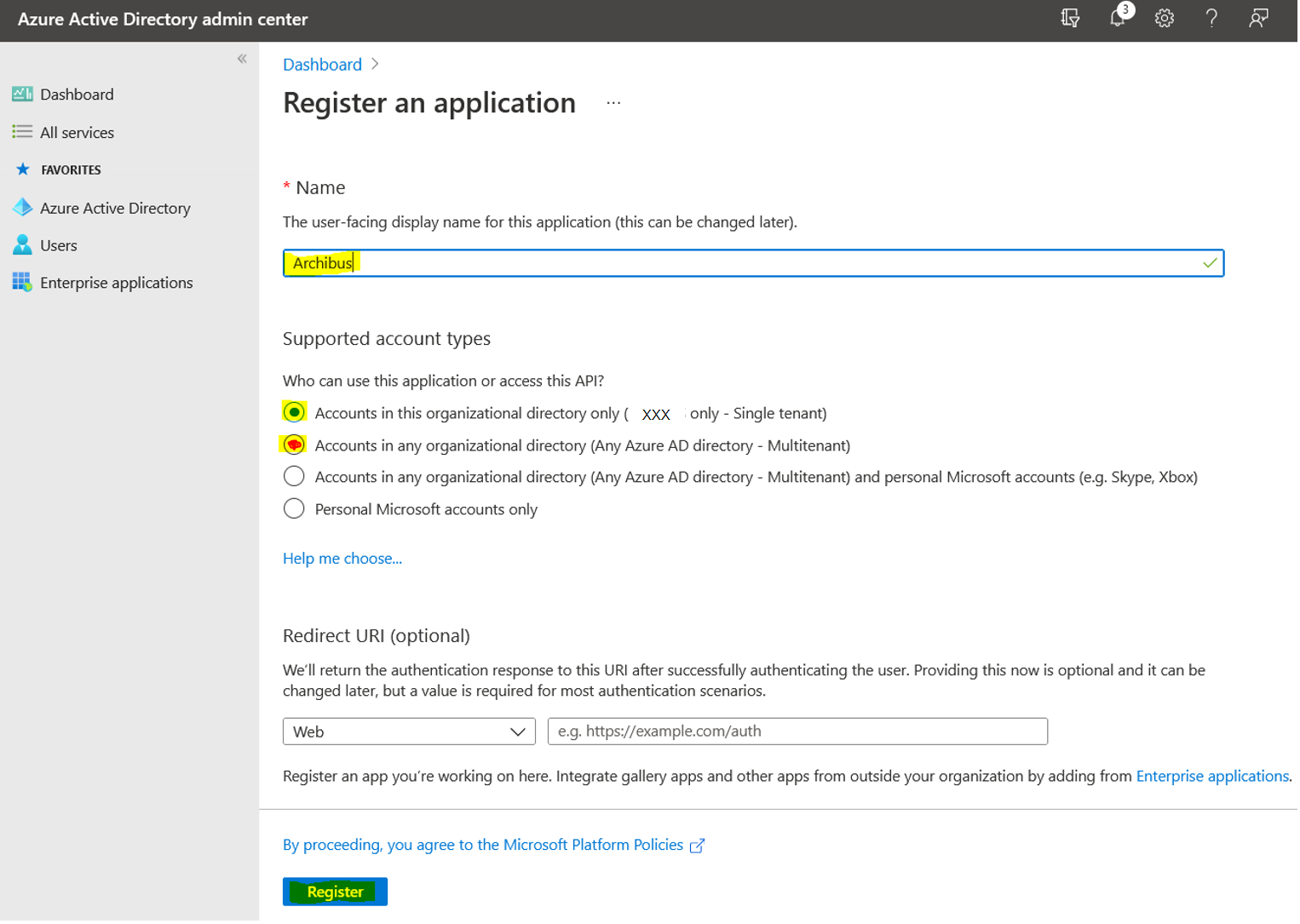
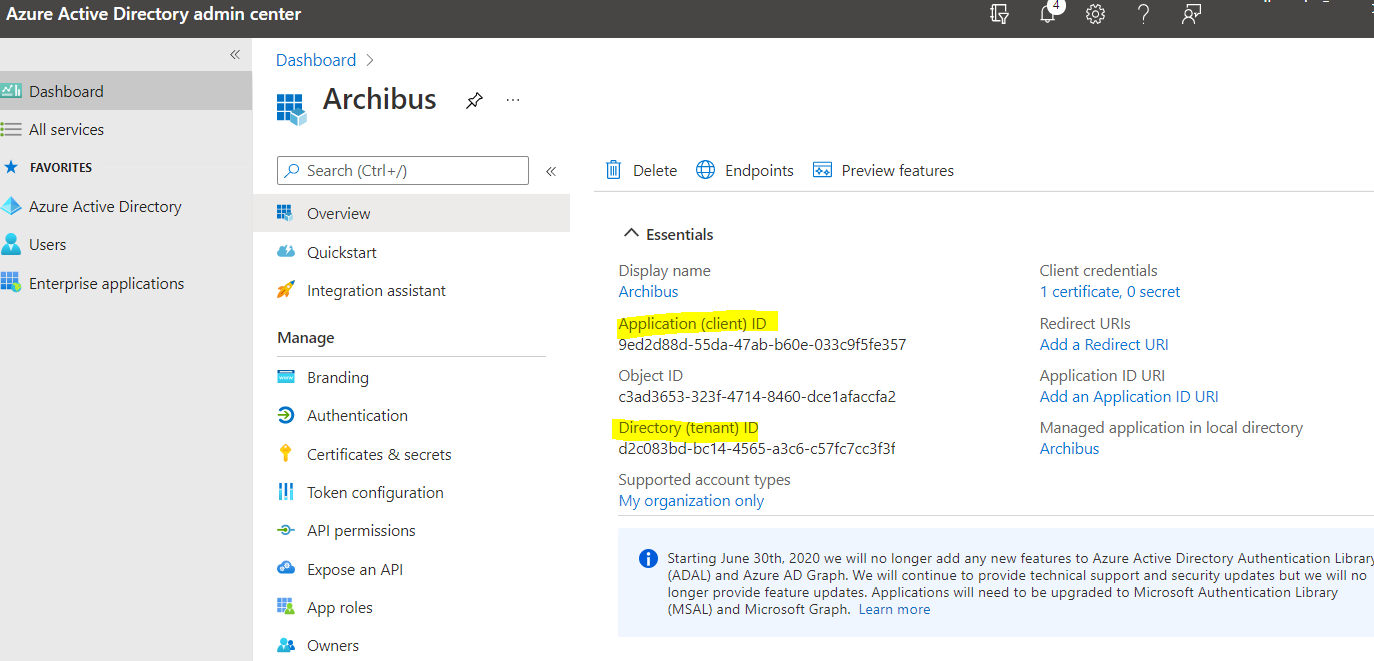
Note the Application (client) ID and Directory (tenant) ID. These values are required to configure Archibus.
-
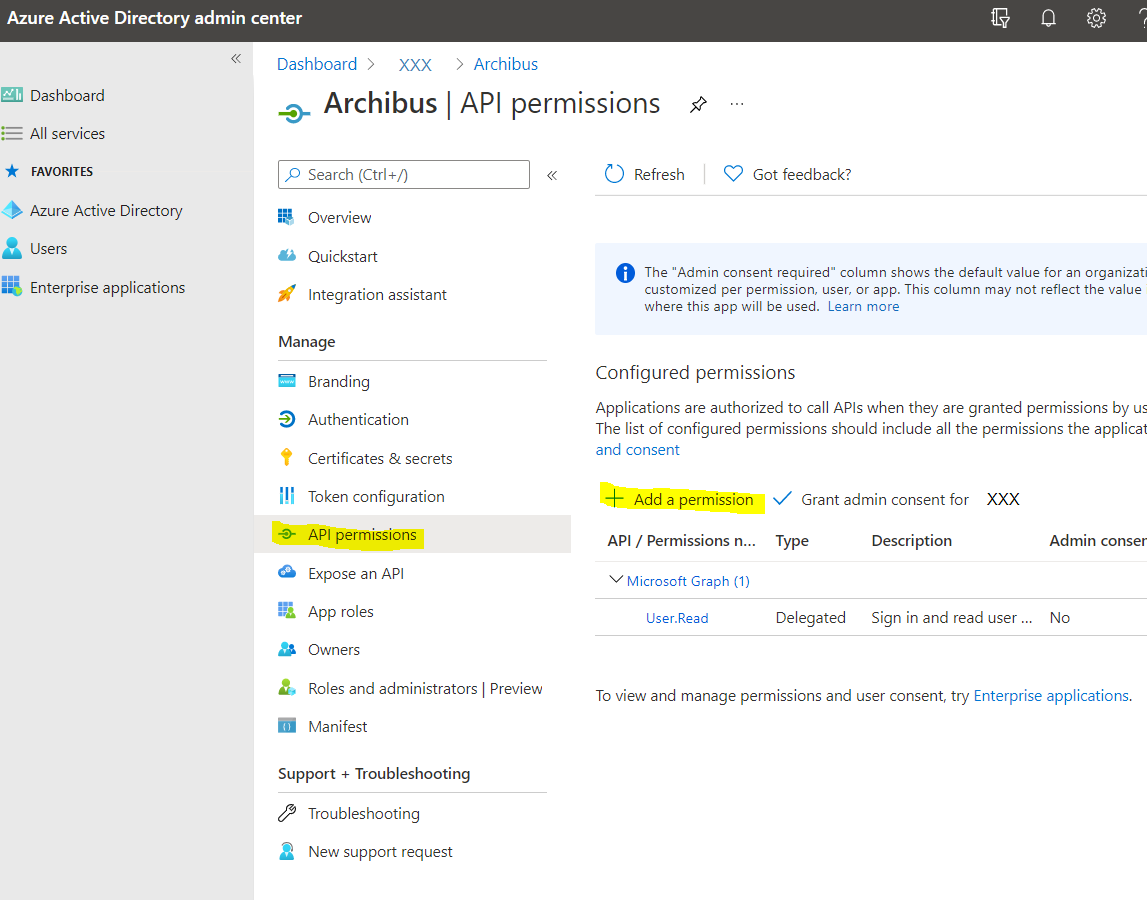
Navigate to API permissions > Add a permission.
-
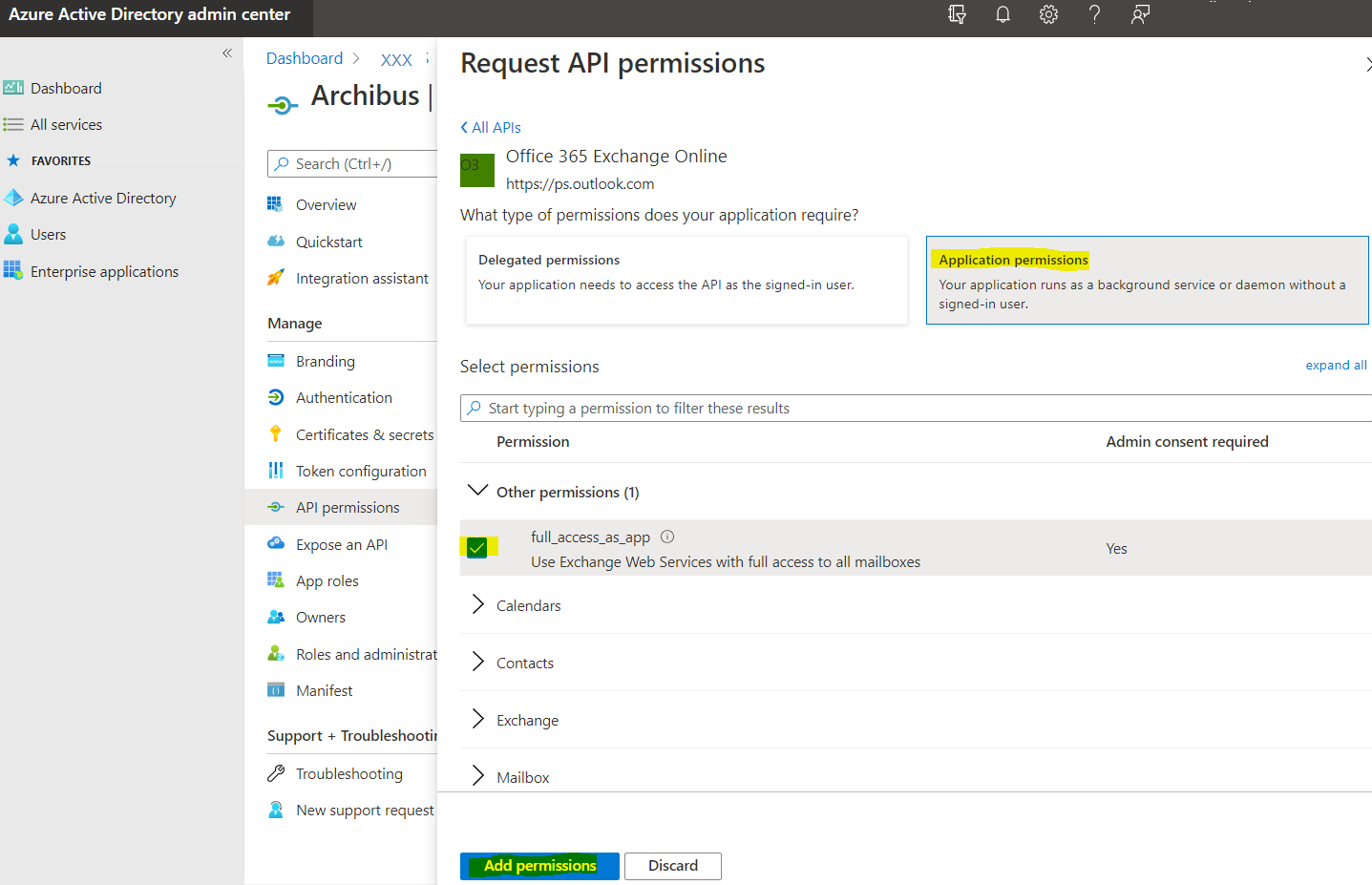
Switch to "APIs my organization uses" and select "Office 365 Exchange Online."

-
Select "Application permissions" > "full_access_as_app." Click "Add permissions."
-
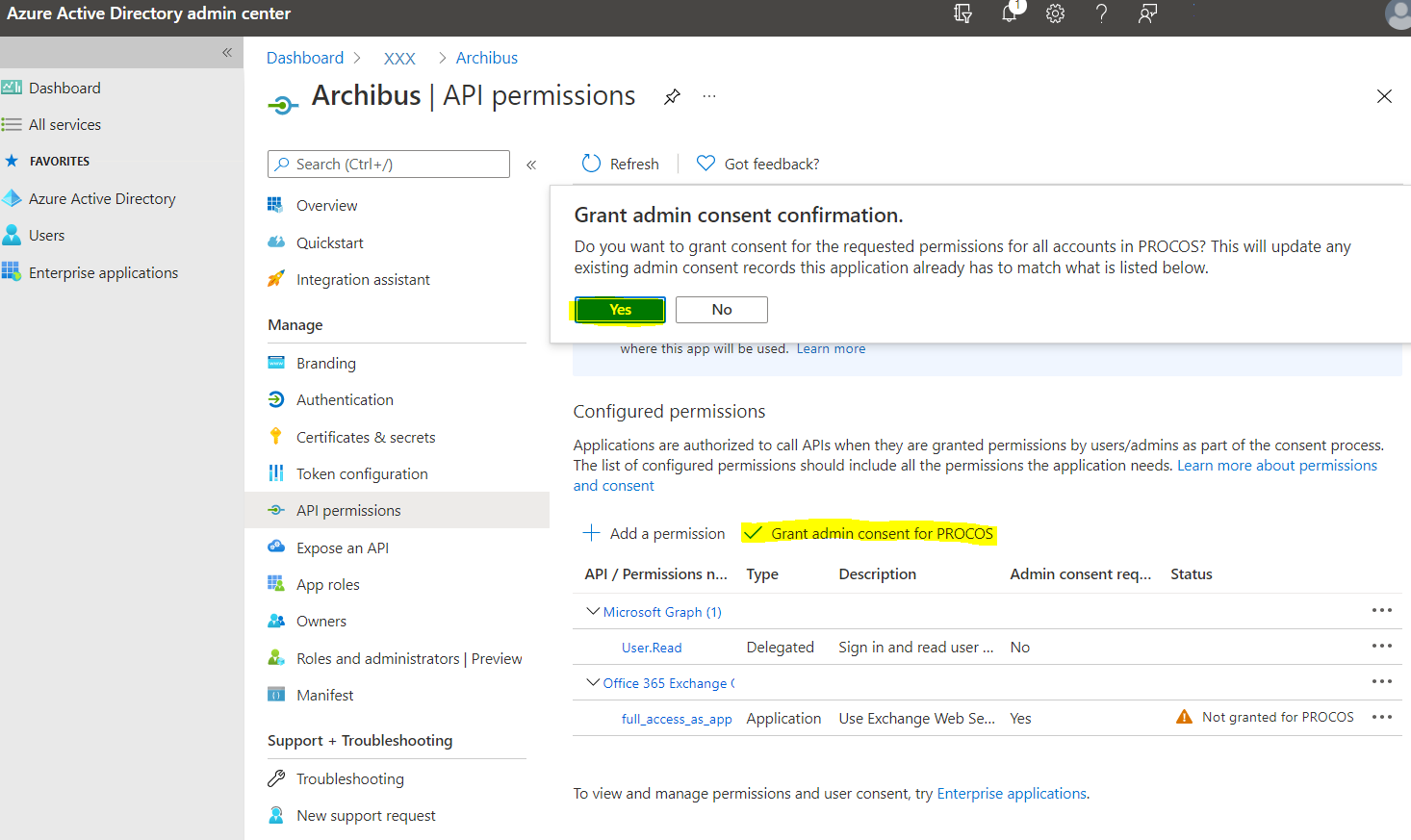
Click "Grant admin consent for …", then click Yes on the confirmation pop-up.
-
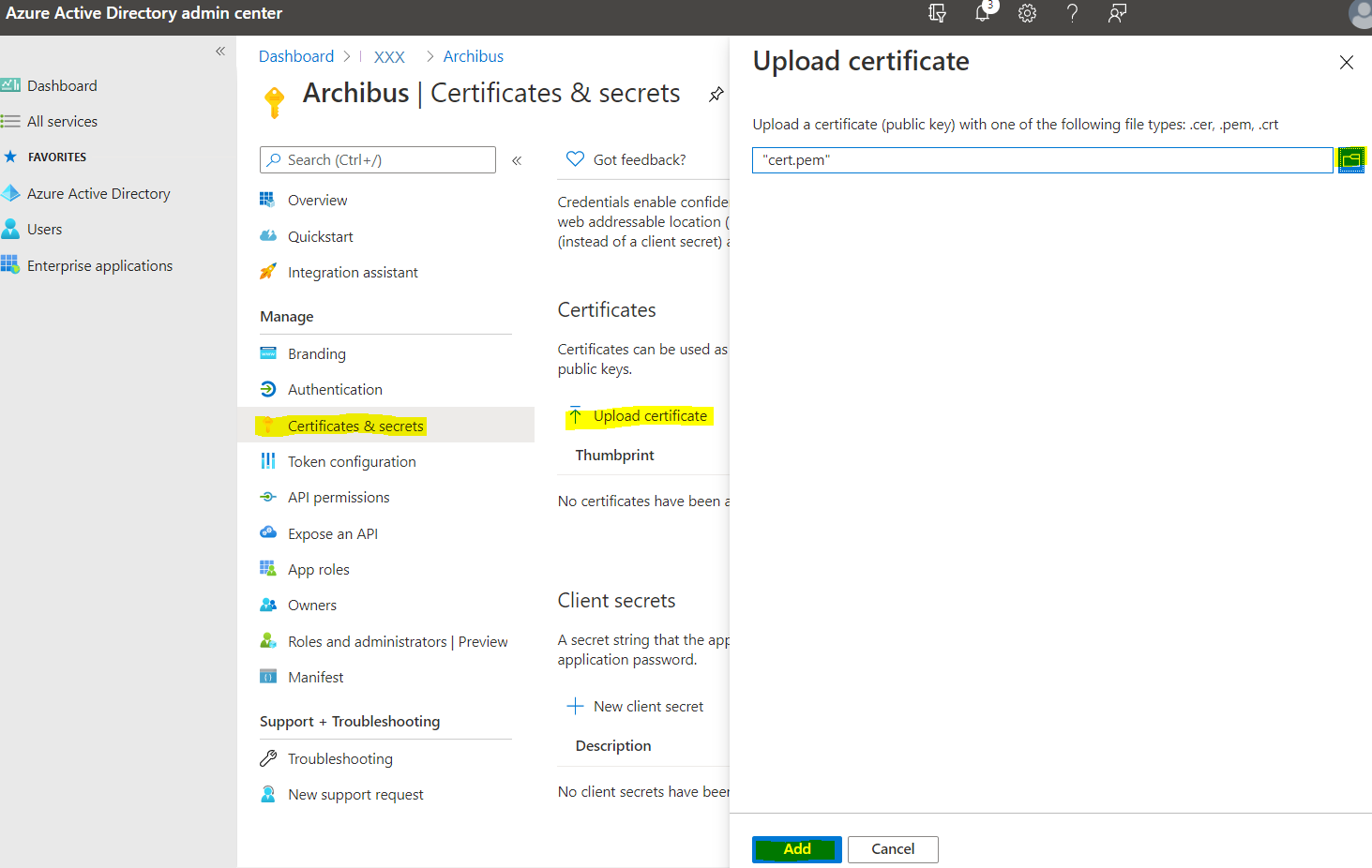
Navigate to Certificates & secrets > Upload certificate. Select the public key of the certificate Archibus will use, then click Add.
Step 2: Restrict Impersonation Access
The application needs access to the mailboxes of all Archibus Outlook Plugin and Web Central users, all room mailboxes and the resource and organizer mailbox.
After completing the above OAuth setup, the application can access all mailboxes on the tenant. The application’s access can be restricted to only the required mailboxes by configuring an application access policy.
Using an application access policy, EWS administrators can limit an app’s access to a specific set of mailboxes by specifying an inclusion or exclusion list. Administrators who want to limit third-party app access to a specific set of mailboxes can use New-ApplicationAccessPolicy PowerShell cmdlet to configure access control.
For more information about application access policies, see Scoping application permissions to specific Exchange Online mailboxes.
Example:
New-ApplicationAccessPolicy -AccessRight RestrictAccess -AppId "e7e…" -PolicyScopeGroupId EvenUsers@AppPolicyTest.com -Description "Restrict this app's access to members of security group EvenUsers."